RISC-V (pronounced “risk-five”) is a modern Reduced Instruction Set Computer (RISC) architecture that has emerged as one of the most important developments in computer architecture in recent decades. Unlike traditional instruction set architectures such as x86 or ARM, RISC-V is open, royalty-free, and extensible, allowing anyone to design processors, experiment with new ideas, or build commercial products without licensing restrictions. Originally developed at the University of California, Berkeley, RISC-V was designed as a clean slate ISA, free from legacy constraints. Its primary goals are simplicity, modularity, scalability, and long-term software compatibility. Because of these characteristics, RISC-V is now used across a wide spectrum—from tiny embedded controllers and IoT devices to high-performance processors, accelerators, and research prototypes. This article explains the RISC-V architecture in detail, including its instruction set structure, registers, execution model, privilege levels, extensions, and overall processor organization.
Design Philosophy of RISC-V
RISC-V follows classic RISC principles while improving upon earlier RISC designs:
- Simple instructions that execute in a small number of cycles.
- Load–store architecture, where only load and store instructions access memory.
- Large register file to reduce memory accesses.
- Fixed base instruction length for simpler decoding.
- No hidden architectural state, such as condition flags.
What makes RISC-V unique is its modular ISA design. Instead of one monolithic instruction
set, RISC-V consists of:
- A mandatory base ISA.
- A set of optional standard extensions.
- Support for custom extensions.
This approach allows designers to build minimal cores for embedded systems or feature-rich processors for high-performance computing, all while maintaining software compatibility.
RISC-V Architectural Overview
At a high level, a RISC-V processor consists of the following major components:
- Program Counter (PC)
- Instruction Fetch Unit
- Instruction Decoder & Control Unit
- Register File
- Arithmetic Logic Unit (ALU)
- Load/Store Unit
- Control and Status Registers (CSRs)
- Memory Interface
- Optional Floating-Point, Vector, and Accelerator Units
RISC-V Architecture Block Diagram
Below is a logical block diagram of a basic RISC-V processor.
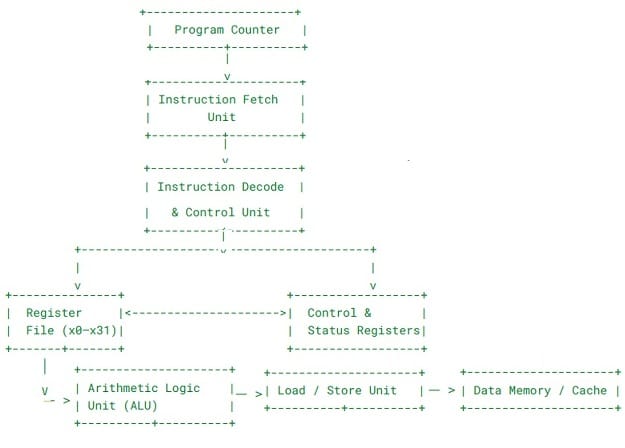
RISC-V Architecture Diagram
Program Counter and Instruction Fetch
The Program Counter (PC) holds the address of the next instruction to be executed. In RISCV:
- Instructions are aligned to 16-bit boundaries
- Base instructions are 32 bits long
- Compressed instructions may be 16 bits
The Instruction Fetch Unit:
- Fetches instructions from memory using the PC
- Increments the PC (normally by 4 bytes)
- Handles control-flow changes due to jumps, branches, and exceptions
Because RISC-V avoids features like branch delay slots, instruction fetch behavior is clean and predictable.
Instruction Decode and Control Unit
The Instruction Decode Unit:
- Interprets the instruction fields (opcode, funct3, funct7, registers, immediates)
- Determines the instruction format (R, I, S, B, U, or J)
- Generates control signals for the datapath
RISC-V instruction formats are carefully designed to:
- Minimize decoding complexity
- Allow opcode reuse
- Support extensibility
This simplicity makes RISC-V suitable for both simple single-cycle cores and deeply pipelined, out-of-order processors.
Register File
The RISC-V base integer ISA defines 32 general-purpose registers:
- Named x0 to x31
- Each register has a width equal to XLEN (32 or 64 bits)
Special Properties:
- x0 is hardwired to zero
- Writes to x0 are ignored
- All other registers are general-purpose
Common ABI names include:
- x1 – return address (ra)
- x2 – stack pointer (sp)
- x10–x17 – function arguments
The large register file reduces memory access frequency, improving performance and energy
efficiency.
Arithmetic Logic Unit (ALU)
The ALU performs:
- Integer arithmetic (ADD, SUB)
- Logical operations (AND, OR, XOR)
- Shifts and comparisons
RISC-V avoids condition flags (like zero or carry flags). Instead:
- Comparisons produce explicit results
- Branch instructions directly compare registers
This design reduces pipeline hazards and simplifies parallel execution.
Load–Store Unit and Memory Access
- RISC-V uses a pure load–store architecture:
- Arithmetic instructions operate only on registers
Memory is accessed only through load and store instructions
Load Instructions:
- LB, LH, LW, LD
- Signed and unsigned variants
Store Instructions:
- SB, SH, SW, SD
Misaligned accesses:
- May cause exceptions
- Or be handled by hardware, depending on implementation
This explicit memory model improves predictability and simplifies formal verification.
Instruction Set Structure
Base Integer ISA
- RV32I or RV64I
- Mandatory for all implementations
Standard Extensions
- M – Integer multiplication and division
- A – Atomic instructions
- F – Single-precision floating point
- D – Double-precision floating point
- C – Compressed instructions
- V – Vector processing
- K – Cryptographic instructions
Extensions are optional but standardized, ensuring portability.
Control and Status Registers (CSRs)
CSRs provide:
- System control
- Exception handling
- Interrupt management
- Performance monitoring
Important CSRs include:
- mstatus – processor status
- mepc – exception program counter
- mcause – reason for trap
- mtvec – trap vector base address
CSRs are accessed using special instructions such as CSRRW, CSRRS, and CSRRC.
Privilege Levels in RISC-V
RISC-V defines a layered privilege model:
1. Machine Mode (M)
- Highest privilege
- Full hardware control
- Mandatory in all implementations
2. Supervisor Mode (S)
- Used by operating systems
- Optional
3. User Mode (U)
- Runs application programs
4. Hypervisor Mode (H) (optional)
- Supports virtualization
This clean separation makes RISC-V suitable for secure and scalable systems.
Interrupts and Exceptions
RISC-V uses a precise trap model:
- Interrupts are asynchronous
- Exceptions are synchronous
On a trap:
- PC is saved in mepc
- Cause is recorded in mcause
- Control jumps to the address in mtvec
Returning from traps uses:
- MRET, SRET, or URET
Pipeline and Performance Considerations
RISC-V’s simplicity enables:
- Efficient pipelining
- Out-of-order execution
- Superscalar designs
Key architectural features that help performance:
- No condition flags
- Simple instruction decoding
- Explicit dependencies
These properties reduce hazards and improve instruction-level parallelism.
Why RISC-V Is Important Today?
RISC-V is transforming the processor ecosystem because it offers:
- Open and royalty-free ISA.
- Educational clarity.
- Research freedom.
- Industrial scalability.
- Future-proof extensibility.
From microcontrollers to AI accelerators and supercomputers, RISC-V provides a common architectural foundation.
FAQs
1. What is RISC-V architecture?
RISC-V is an open-standard, royalty-free instruction set architecture (ISA) based on Reduced Instruction Set Computer (RISC) principles. It allows anyone to design, implement, and customize processors without licensing fees, making it popular in education, research, and industry.
2. Why is RISC-V considered an open ISA?
RISC-V is considered open because its specifications are freely available and can be used without paying royalties. Designers can build commercial or academic processors and even add custom extensions while maintaining compatibility with the base ISA.
3. What are the main components of RISC-V architecture?
The main components include the Program Counter, Instruction Fetch Unit, Instruction Decoder, Register File, ALU, Load/Store Unit, Control and Status Registers (CSRs), and optional units such as Floating-Point and Vector processors.
4. How many registers are there in RISC-V?
RISC-V defines 32 general-purpose integer registers, named x0 to x31. Register x0 is hardwired to zero, while the remaining registers are used for arithmetic operations, function calls, and data storage.
5. What is the load-store architecture in RISC-V?
In a load-store architecture, only load and store instructions access memory. All arithmetic and logical operations are performed on registers, which improves performance and simplifies hardware design.
6. What are RISC-V extensions?
RISC-V extensions are optional standardized instruction sets that add functionality to the base ISA. Common extensions include M (multiplication/division), A (atomic operations), F and D (floating-point), C (compressed instructions), and V (vector processing).
7. What privilege modes are supported in RISC-V?
RISC-V supports multiple privilege modes, including Machine mode (M), Supervisor mode (S), and User mode (U). An optional Hypervisor mode (H) is available for virtualization support.
8. What is the purpose of Control and Status Registers (CSRs) in RISC-V?
CSRs are used to control processor behavior and manage exceptions, interrupts, privilege levels, and performance counters. Examples include mstatus, mepc, mcause, and mtvec.
9. How does RISC-V handle interrupts and exceptions?
RISC-V uses a precise trap mechanism. When an interrupt or exception occurs, the processor saves the program counter and cause information in CSRs and transfers control to a trap handler defined by the mtvec register.
10. Why is RISC-V important for the future of processors?
RISC-V is important because it enables innovation through open standards, supports custom hardware accelerators, reduces dependency on proprietary ISAs, and scales from embedded systems to high-performance computing.
11. Is RISC-V suitable for beginners learning computer architecture?
Yes, RISC-V is ideal for beginners because of its clean design, simple instruction formats, absence of legacy features, and excellent documentation, making it easier to understand core architectural concepts.
12. How is RISC-V different from ARM architecture?
Unlike ARM, RISC-V is completely open and royalty-free. It allows designers to create custom extensions without vendor approval, while ARM uses a licensed and proprietary instruction set.
Conclusion
In summary, the RISC-V architecture represents a major shift in how processors are designed and studied. By combining simplicity, modularity, and openness, it enables innovation at every level—from classroom learning to cutting-edge research and commercial products. Understanding RISC-V architecture not only strengthens knowledge of modern computer architecture but also prepares students and engineers for a future where customizable, open hardware plays a central role in computing.