CoAP (Constrained Application Protocol) is an application layer protocol, introduced in 2014 by the Internet Engineering Task Force and specified within IETF RFC 7252. This protocol was web-based which resembles HTTP, and thus mainly designed for constrained devices. CoAP small and low-power devices to connect the IoT (Internet of Things) and also converse with the wider Internet with the least resources. This protocol has a minute base specification that can be expanded through extra functionality when required. So, it functions over UDP and gives a request/response interaction model between application endpoints by allowing interoperability amongst different kinds of devices. This protocol is highly consistent which makes it appropriate for IoT devices and they frequently operate within challenging network situations. This article provides an overview of the CoAP protocol, its working, and its applications.
What is the CoAP Protocol?
The constrained application protocol is a web transfer protocol that works with constrained networks & nodes. Generally, these networks are used in Internet of Things (IoT) applications, wherever devices have partial memory, power resources, and processors. This protocol is very simple, efficient, and has low overhead which makes it perfect for machine-to-machine-based communication. CoAP is mainly designed to allow simple and constrained devices to connect to the IoT even through limited networks through low availability and low bandwidth. This protocol is used normally for M2M (machine-to-machine) applications like smart energy & building automation.
How does CoAP Work?
CoAP works as a type of HTTP for limited devices by allowing equipment like actuators or sensors to communicate on the Internet of Things. This protocol is mainly designed for reliability within high congestion and low bandwidth through its low network overhead and less power consumption. CoAP in a network can continue to work with much congestion (or) limited connectivity wherever MQTT protocols fail to exchange data and converse efficiently.
In addition, the efficient and straight protocol features allow devices to operate in poor signal quality to transmit their data consistently or allow an orbiting satellite to keep its distant communication effective. This protocol can also support networks through several nodes.
COAP protocol utilizes UDP as the fundamental network protocol and is normally a client-server-based IoT protocol wherever the client makes a request & the server sends back a reply because it takes place within HTTP.
CoAP Layer
The CoAP protocol simply works through its two layers which are discussed below.
Messages Model
Messages model makes UDP transactions achievable in the CON (confirmable) or NON (non-confirmable) format at endpoints. Each CoAP message has a distinct identification to keep the message duplication possibilities at bay.
The three main parts involved in making this layer are the binary header, the second computer option, and the third payload. As we discussed earlier, confirmable texts are consistent and simple to design messages that are quick & are resent until the confirmation receipt of successful delivery with message identification.
Request (or) Response Model
The request or response layer protects CON & NONmessage requests where these requests’ acceptance mainly depends on the availability of servers. If it is idle, then the server handles the request immediately and if it is CON, then the client gets an ACK for it.
So if the ACK is divided as a Token and changes from the identification, it is important to map it correctly by simply matching the pairs of request-response. If there is a wait or delay involved, then ACK is transmitted although as an empty text. Whenever its turn appears, then the request is simply processed & the client will get a fresh CON.
The Request/Response key traits model is mentioned next:
- Request (or) response codes for this protocol are similar to the HTTP, apart from the reality that they are within the binary format in CoAP protocol’s case.
- Request methods to make calls are simply declared in the procedure.
- A CON response could be either stored in an ACK message (or) forwarded as CON/NON.
CoAP Methods
The CoAP methods are discussed below.
- The GET method is utilized to recover resource data recognized by the request URI. So, a 200(OK) response is sent in reply to the GET method success.
- The POST method is useful in creating a new subordinate resource in the parent URI demanded by it toward the server. A 201 code response is sent on successful resource formation on the server whereas on malfunction, a 200 code response is sent.
- The DELETE method simply deletes the identified resource by the requested URI & a 200 code response is sent on the victorious operation.
- The PUT method simply creates or updates the resource recognized by the request URI through the included message body. So, this is considered merely as a modified resource version if it exists at the particular URI already, or else a new resource with that URI can be created. So, a 200 response code is received in the past case while a 201 response code is obtained in further cases. If the resource is neither formed nor changed then an error reply code will be sent.
- The most basic variation between HTTP and CoAP is that CoAP protocol describes a new method whereas HTTP does not. So this method is known as the Observe method which is much related to the GET method additionally with an observe option. So this alerts the server to transmit each update regarding the resource to the client. Thus, the server transmits a response to the client upon any change within the resource. So these responses could be either sent directly otherwise they are piggy-backed.
CoAP Features
CoAP features are discussed below.
RESTful Architecture
CoAP utilizes a Representational State Transfer or RESTful architecture which follows simply a set of constraints. So, these constraints allow it to efficiently function above a big and distributed network. The data as well as functionality within a RESTful system are considered resources that are accessed with a normal uniform interface.
The RESTful architecture allows this protocol to provide a high range of interoperability between different kinds of devices. In addition, it also makes it simple for developers to make applications that utilize this protocol, because they can utilize typical HTTP methods to communicate with resources like; POST, GET, DELETE & PUT.
Built-In Discovery
The in-built discovery mechanism simply allows various devices to determine resources on other types of devices without needing any prior information about their existence. So this is particularly helpful within IoT networks, wherever devices may be continually joining & departing the network.
This in-built discovery feature in this protocol is attained by using a familiar ‘core’ resource that gives a list of accessible resources on a device. So this resource is simply queried by another type of device over the network by permitting them to find out what resources are accessible and how to communicate with them.
Asynchronous Message Exchanges
CoAP protocol simply supports asynchronous message connections, which is essential for IoT networks wherever different devices may not be available or connected always. So a device can send a request to another device with asynchronous message exchanges, and after that, it continues with different tasks exclusive of waiting for a reply. This response can be processed whenever it appears even if postponed.
This feature utilizes a message identifier within every CoAP protocol message to allow a device to match responses with requests. So this in combination with the capacity to retransmit lost messages ensures a high range of reliability within exchanges of messages.
Optional Reliability through Confirmable Messages
This protocol provides optional reliability with the help of confirmable messages. Once a device sends a certain message it guesses an acknowledgement mainly from the receiver. If no acknowledgment is obtained in a certain time, then the message will be transmitted again. This feature allows this protocol to provide consistent communication in situations where network connectivity is defective so that devices can make sure that critical messages are obtained & processed.
CoAP Protocol Architecture
The CoAP protocol architecture is shown below which expands common HTTP clients to clients with resource constraints called CoAP clients. This architecture includes two fundamental elements WWW & the constraints ecosystem. The server checks and assists in communication happening with HTTP and CoAP whereas the Proxy device links the gap between the constrained environment & usual internet environment based on HTTP protocols. So both CoAP & HTTP protocol messages are protected by the same server.
CoAP simply allows HTTP clients to communicate (or) exchange information or data with each other in resource constraints. To understand this architecture, gaining connections with some main terms is fundamental.
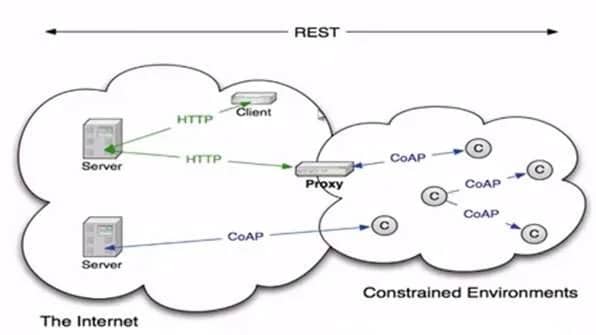
CoAP Architecture
Endpoints are known as nodes that the host has the familiarity of;
- The client sends requests & gives replies to incoming requests;
- The server obtains & forwards requests. In addition, it also obtains and forwards the received messages in reply to the processed requests.
- The sender makes & sends the actual message.
- The recipient obtains the data sent through the client (or) forwarded through the server.
CoAP Message Exchanges
There are two modes where CoAP messages get exchanged between the CoAP Client & CoAP Server viz. with separate response and exclusive of separate response.
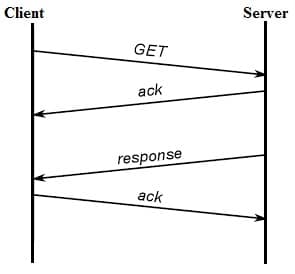
CoAP Protocol Message Exchanges
- The server notifies the client with a separate response about the request message receipt. This will improve processing time however assist in avoiding avoidable retransmissions.
- CoAP is an unreliable protocol because of the use of UDP. Therefore CoAP protocol messages are unordered (or) will get lost whenever they appear at the destination.
- To make this protocol reliable, wait and stop with exponential backoff retransmission characteristic is included in it. So, duplicate detection can also be introduced.
Message Format
The messages in the CoAP protocol are encoded within binary format. Similar to other message formats, this protocol message includes a header as well as a payload section with an optional section. So CoAP header size is 32 bits which is fixed for each CoAP message while the other portion of the message is the optional part which comprises payload and variable size tokens which range from 0-8 bytes. So this message format includes the different fields which are discussed below.

Message Format
- The version field size is 2 bits which signifies the CoAP protocol version.
- The type field size is 2 bits so there are four kinds of messages; first confirmable, second non-confirmable, third acknowledgment, and fourth reset which are signified by the 00, 01, 10 & 11 bit patterns correspondingly.
- The option count field size is 4 bits which means there are 16 total achievable options within the header.
- The code field size is 8 bits which specifies whether the message is vacant, request message (or) reply message.
- The message ID field size is 16 bits which is used to notice the duplication of message and message types.
- The tokens size field is a variable that ranges from 0-8 bytes, so it is utilized to match a reply through request.
- The options field within the CoAP message includes a variable size that describes the kind of payload message.
- The payload field similar to the options field has an uneven size. So the payload of requests (or) responses is normally an illustration of the requested resource (or) the requested action result.
MQTT Vs CoAP Protocol
The difference between MQTT and CoAP includes the following.
|
MQTT |
CoAP |
| MQTT is a messaging protocol used to create communication between several devices. | CoAP is a special web transfer protocol that functions with constrained nodes as well as networks. |
| MQQT stands for message queuing telemetry transport. | CoAP stands for constrained application protocol. |
| Its main purpose is to message and communicate with IoT. | It is designed mainly for resource-constrained devices within IoT. |
| The transport protocol used in this is TCP. | The transport protocol used in this is UDP. |
| It maintains constant connections. | It maintains a very lightweight connection setup. |
| The communication style is the publish or subscribe model. | The communication style is a request or response model. |
| Its header size is two two-byte fixed headers. | Its header size is four four-byte fixed headers. |
| Message types are; subscribe, publish, connect, disconnect many more. | Message types are; POST, GET, DELETE, PUT, etc. |
| Resource discovery is not inherent, thus it needs extra mechanisms. | Resource discovery is in-built resource discovery throughout CoRE link format. |
| The security used is SSL/TLS for encryption & authentication. | Datagram transport layer security is used for safe communication. |
| This protocol supports message payload compression. | It supports simple message payload compression. |
| It doesn’t have header compression. | This protocol utilizes CoAP-specific header compression. |
| MQTT is designed to be used in a wide range of Internet of Things applications | It is designed for constrained devices with partial resources. |
Advantages & Disadvantages
The advantages of the CoAP protocol include the following.
- CoAP is a simple protocol that uses less overhead because of operation above UDP. This protocol allows little wake-up times & long sleepy states which helps in attaining longer battery life to utilize in IoT & M2M communication.
- This protocol utilizes DTLS or IPSEC to provide safe communication.
- Synchronous communication is not required.
- This protocol has less latency as compared to HTTP.
- This protocol consumes low power.
- It utilizes the ACK message, thus it becomes consistent and avoids preventable retransmissions.
- CoAP protocol is the best protocol choice mainly for home communication networks.
- This protocol is lightweight, fast, and uses more efficient binary encoding.
The disadvantages of the CoAP protocol include the following.
- This protocol is unreliable because it uses UDP, so protocol messages will get lost whenever they reach the destination. To make this protocol reliable, wait & stop with the incorporated exponential backoff retransmission feature.
- It recognizes every message receipt, thus improving processing time. Furthermore, it does not confirm whether the expected message has been correctly decoded or not.
- This protocol is unencrypted and utilizes DTLS to provide safety at the implementation overhead cost.
- This protocol has communication problems for devices behind Network Address Translation (NAT).
CoAP Protocol Applications
The applications of the CoAP Protocol include the following.
Home Automation Systems:
CoAP is being used increasingly in smart home automation systems because of its high reliability & low overhead. Different devices in these systems like thermostats, security cameras, and lights can all interact with the CoAP. So this allows for a higher range of interoperability & makes it simple to include new devices in the network.
Sensors & Actuators:
Sensors as well as actuators can communicate with CoAP by allowing real-time monitoring also industrial process control. In these scenarios, the protocol’s support mainly for multicast communication is mainly helpful, because it permits a single device to converse with several others at the same time.
Healthcare:
CoAP is very popular in healthcare and wearable device applications which frequently use very small and battery-powered devices that require to converse with a central server.
Energy Management Systems:
This protocol is utilized in energy management systems, wherever it permits for real-time monitoring & energy usage control. Smart meters & energy management controller devices use this protocol to converse with each other by providing a high range of control above energy usage.
- Smart cities remotely monitor the distribution and power generation. The CoAP sensors could be fixed within the transformers & the data could be transmitted over 6LowPAN or GPRS.
- At present, tanks & armories are fitted through sensors so that data can be remotely conversed exclusive of any interference.
- The CoAP could notice any intrusion which makes them able to transmit more information even in low bandwidth networks.
- The aircraft sensors as well as actuators could be allied with other types of sensors & communication can happen with smart CoAP-based actuators & sensors.
Thus, this is an overview of the CoAP protocol, its working, and its applications. This is a specialized constrained application protocol designed for constrained devices. This protocol allows low-power and small devices to connect to the IoT (Internet of Things). So, this protocol simply allows mainly these devices to communicate with the wider Internet through the least resources.
This protocol includes a tiny base specification that can be expanded with additional functionality whenever required. It works over UDP and gives a request or response interaction model between application endpoints by allowing interoperability among various kinds of devices. This protocol can also be extremely reliable in confirming message delivery even in limited network connectivity cases. So this makes it appropriate for IoT devices, which frequently work within challenging network situations. Here is a question for you, what is MQTT?